End to end Encryption with AKS and API Management
I was trying to host micros services in aks behind APIM and wanted to provide end to end encryption. One of the point I was evaluating was Azure AppGateway Ingress Controller( AGIC) vs NGINX. After following this and based on huge workload requirment AKS Ingress Performance Testing: Nginx vs AppGW (AGIC). I have chosen NGINX as my Ingress Controller.
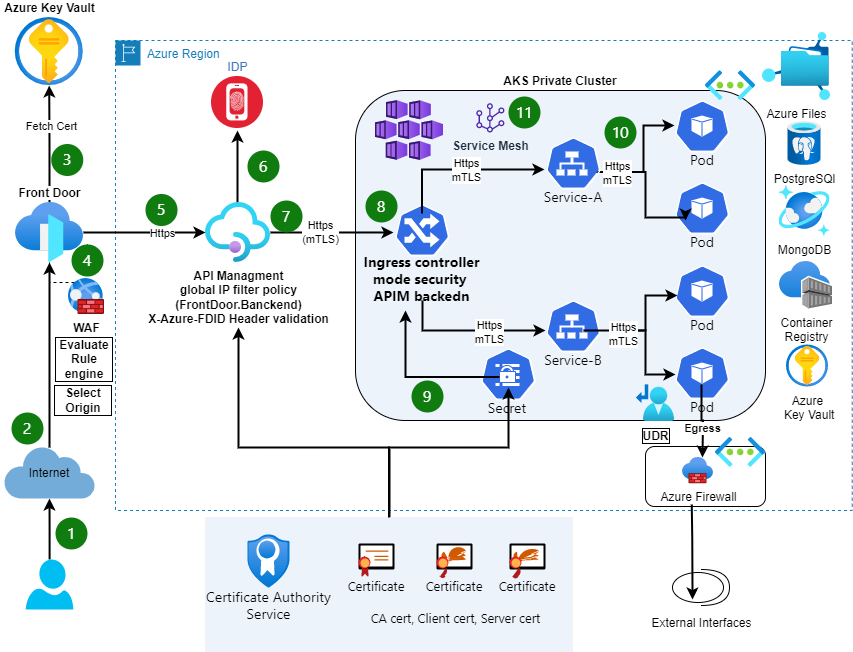
Data Flow for Ingress
- A user requests to the application endpoint from the internet.
- Azure Front Door receives traffic as HTTPS and presents a PFX certificate previously loaded from Azure Key Vault to the user.
- Azure Front Door uses private keys to decrypt traffic (SSL offload), performs web application firewall inspections, and re-encrypts traffic by using public keys (end-to-end encryption).
- Azure Front Door applies rules based on the Origin groups and sends traffic to the API Management backend pool over HTTPS.
- API Management receives traffic as HTTPS with custom domain PFX certificates. It also validates the Front Door backend IP address using the Global IP filter and X-Azure-FDID header.
- IDP provides authentication and applies API Management policies via OAuth and client certificate validation. To receive and verify client certificates over HTTP/2 in API Management, In APIM Negotiated client certificate is enabled on the Custom domains blade in API Management.
- API Management sends traffic via HTTPS to an ingress controller for an AKS private cluster.
- The AKS ingress controller receives the HTTPS traffic and verifies the PEM server certificate and private key(mTLS).
- The ingress controller processes TLS secrets (Kubernetes Secrets) by using cert.pem and key.pem. The ingress controller decrypts traffic by using a private key (offloaded). For enhanced security secret management that’s based on requirements, CSI driver integration with AKS is available.
- The ingress controller re-encrypts traffic by using private keys and sends traffic over HTTPS to AKS pods.
- Inside AKS cluster mTLS is enabled using OSM (Open Service Mesh).
Data Flow for Egress
- When Pod will access any external service, the request will reach to Firewall.
- A route table and user-defined routes are used to route the outbound traffic from the private AKS cluster to the Firewall.
- Firewall will do the host validation and after nating will send the request to the external service.